Vulnerability Assessment
Vulnerability Assessment identifies and evaluates weaknesses in your organisation’s IT systems, networks, applications, and devices. It helps you understand where security gaps exist — like outdated software, open ports, or misconfigured settings — that attackers could exploit. The process involves scanning your systems using specialised tools, analysing the results, and providing a report with identified vulnerabilities, their risk levels, and recommendations on how to fix them.
Key Benefits of the Service
✅ Protect sensitive business and customer data
✅ Ensure compliance with GDPR, Cyber Essentials, ISO 27001
✅ Avoid costly data breaches and reputational damage
✅ Part of overall Security Assessments
What’s Included in the Service
✅ Network, server, and endpoint assessments
✅ Web application vulnerability testing
✅ Cloud security assessment (if applicable)
✅ Prioritised risk-based reporting
✅ Expert remediation guidance
✅ Post-assessment technical support
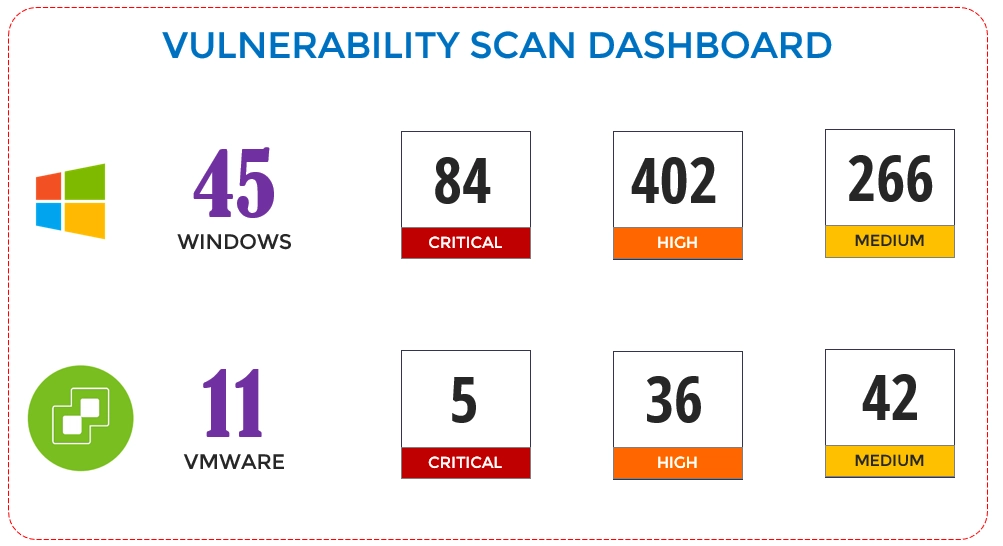
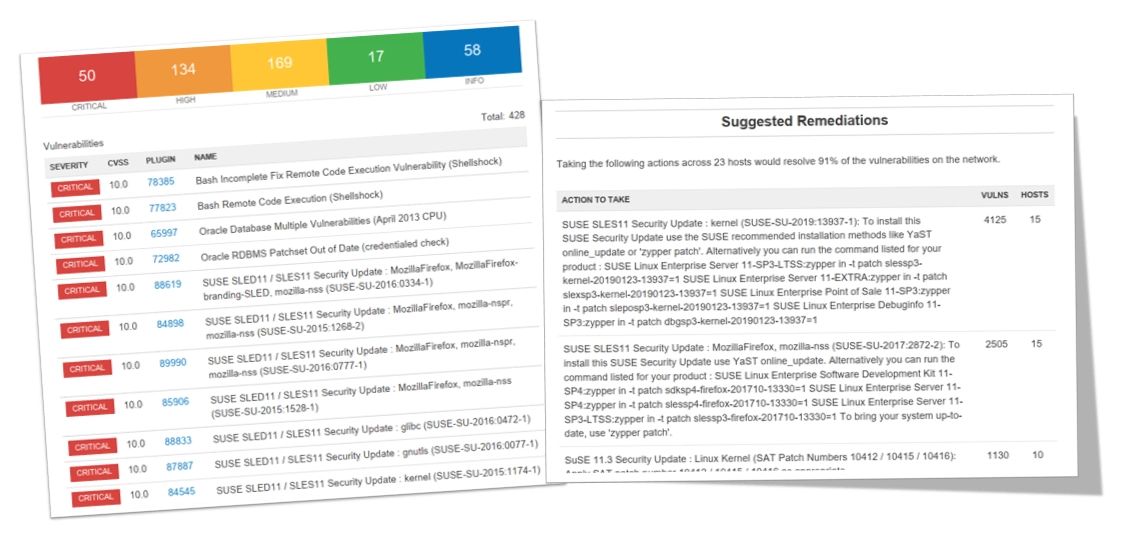
Sample Deliverables
Discovery & Scoping
We define your assessment scope, assets, and priorities.
VA Scan & Analysis
We use industry-standard tools to scan your systems and analyse findings.
Reporting
You receive a clear, risk-ranked report with tailored remediation advice.
Follow-up Support
Our security experts remain available for follow-up guidance and patch validation.
Key Features of Our Assessments
Survey and Data Gathering
Consultants will examine all the components in the IT infrastructure and acquire data by:
– Physical survey of data centres, computer rooms
– Interviews with IT staff
– Inspection of systems, configurations, documentation
Documentation
Work products in this phase include:
– Documentation of servers, networks, applications, services, etc.
– Topology and connectivity diagrams
– Server and equipment lists
Assessment & Analysis
Adequacy of controls will be tested against
– Controls based on standards/frameworks:
– ISO27001/PCI-DSS/NIST etc
– Test controls in all security domains
– Technology assessment by VA tools
Quality Reports
Summary reports and detailed reports will be submitted. The granularity of reports and types of reports vary according to the scope and requirements of the client.
Recommendations
Based on the business requirements:
– Highlighting areas requiring immediate action
– Configuration changes or system upgrades
– Implementation of new controls
Presentation & Workshop
– Presentation of findings: Executive Summary
– Discussing recommendations with the team
– Workshop with tech and admin teams






