Compliance Reviews: ISO27k1/SOC2/
We help organisations assess their readiness and compliance with global and regional information security standards. Our Service Compliance Review identifies gaps, validates current controls, and ensures you meet the technical, legal, and operational requirements for frameworks like ISO 27001, HIPAA, SOC 2, NESA, GDPR, and more.
We deliver expert-led assessments, practical recommendations, and clear action plans to improve your compliance posture and minimise risk exposure.
📌 Major Compliance Standards We Cover:
ISO/IEC 27001:
International gold standard for Information Security Management Systems (ISMS). Protects sensitive information through risk-based controls.
HIPAA:
Mandatory for healthcare organisations handling protected health information (PHI). Ensures confidentiality, integrity, and availability of health data.
SOC 2:
Designed for service providers storing customer data in the cloud. Focuses on security, availability, processing integrity, confidentiality, and privacy.
GDPR:
European data privacy regulation ensuring lawful, transparent processing and protection of personal data.
NESA (UAE):
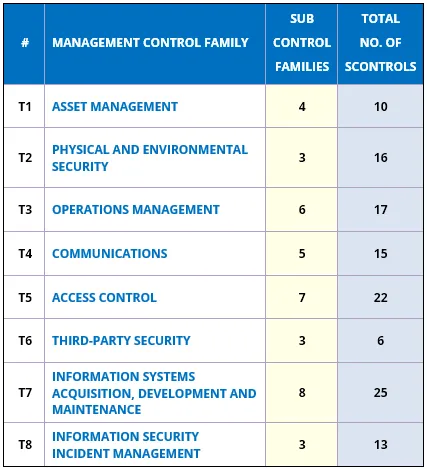
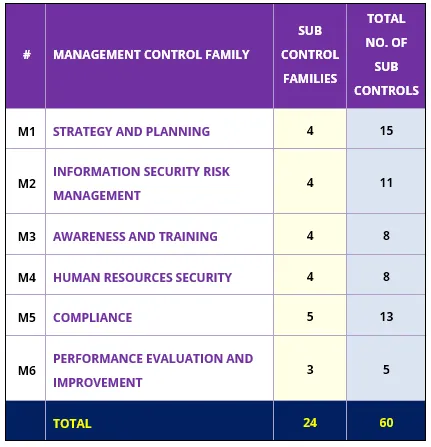
UAE’s National Electronic Security Authority framework for government entities and critical infrastructure, covering cybersecurity governance, policies, and controls. (see below)
🎯 Benefits of this Service
- Ensure regulatory and contractual compliance
- Identify and close control gaps
- Minimise audit failure risk
- Improve information security posture
- Protect customer and business data
- Build client and partner trust
- Accelerate audit readiness
- Reduce legal and financial exposure
- Standardise security practices company-wide
- Support market expansion and tender eligibility
📦 Key Deliverables
- Compliance Gap Analysis Report
- Control Maturity Assessment
- Detailed Compliance Roadmap
- Prioritised Remediation Plan
- Risk Register (if applicable)
- Executive Summary Presentation
- Compliance Documentation Templates
- Readiness Certification Statement
📋 Key Tasks
- Compliance Framework Scoping
- Review of Existing Policies & Controls
- Gap Analysis Against Chosen Standards
- Risk Assessment (where applicable)
- Evidence Review & Documentation Check
- Maturity Level Scoring
- Control Effectiveness Validation
- Incident Response Capability Review
- Staff Awareness Check
- Third-Party Security Risk Review
- Data Privacy Compliance Review
- Technical Security Control Evaluation
- Business Continuity & Disaster Recovery Review
- Prioritised Remediation Recommendations
- Final Compliance Review Presentation