IT Documentation Service
In today’s complex IT environments, proper documentation of systems, networks, and configurations is often overlooked — yet it remains one of the most critical foundations for operational stability, security, and business continuity. Comprehensive and well-maintained systems and networking documentation ensures that your IT infrastructure is visible, manageable, and secure, while also supporting audits, troubleshooting, incident response, and change management processes.
Why Systems & Networking Documentation is Necessary
Without clear documentation, organisations risk losing vital knowledge about their infrastructure, system dependencies, and network configurations. In dynamic environments where systems evolve rapidly and new applications are frequently introduced, undocumented changes can lead to operational issues, prolonged outages, and security vulnerabilities.
From a governance and compliance perspective, major standards like ISO/IEC 27001, NIST CSF, PCI DSS, and HIPAA require organisations to maintain up-to-date IT documentation. This includes network diagrams, asset inventories, configuration details, data flow maps, and access control matrices. During audits or security incidents, the absence of accurate documentation can lead to compliance failures, increased recovery time, and difficulty in assessing the impact of breaches or misconfigurations.
Well-maintained documentation also benefits operational teams by providing clarity on system architecture, facilitating quicker issue resolution, and enabling smooth knowledge transfer between personnel. In environments where external consultants or third-party vendors are involved, clear and current documentation reduces risks associated with service disruptions, miscommunications, and security gaps.
Our Documentation Service Offering
Our Systems & Networking Documentation Service is designed to help organisations build, review, and maintain comprehensive documentation of their IT environments. We take a structured and standards-aligned approach to ensure that documentation is complete, consistent, and secure.
We begin by conducting a discovery exercise, reviewing your existing documentation (if any), and identifying gaps. Our team collaborates with your IT and security teams to collect and verify infrastructure details, including servers, network devices, cloud platforms, applications, data flows, and security controls.
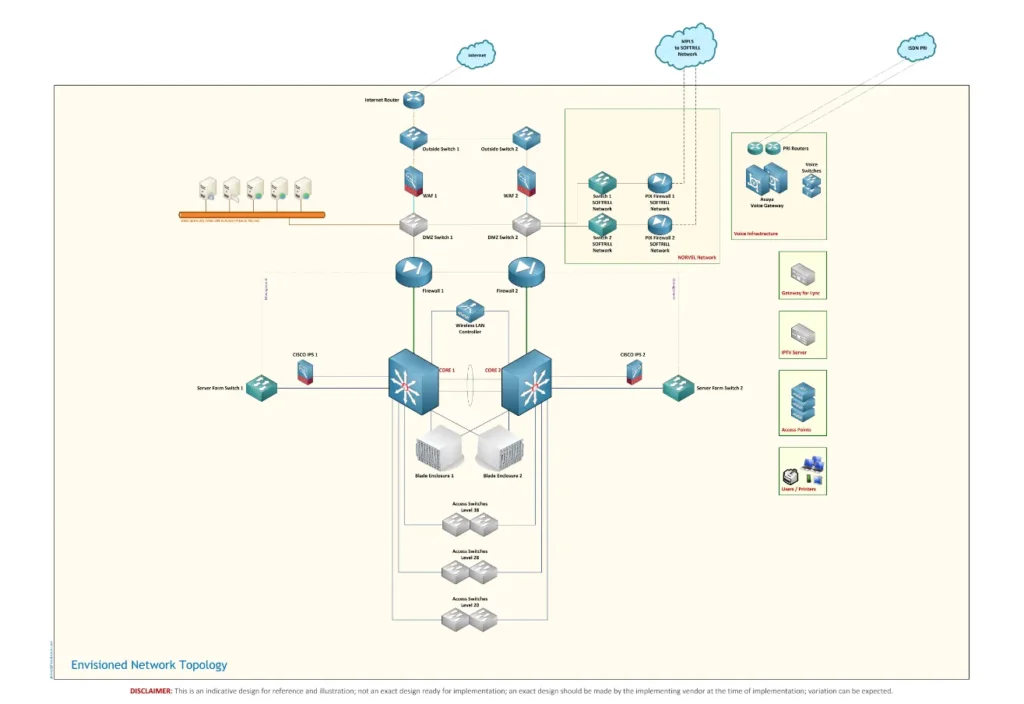
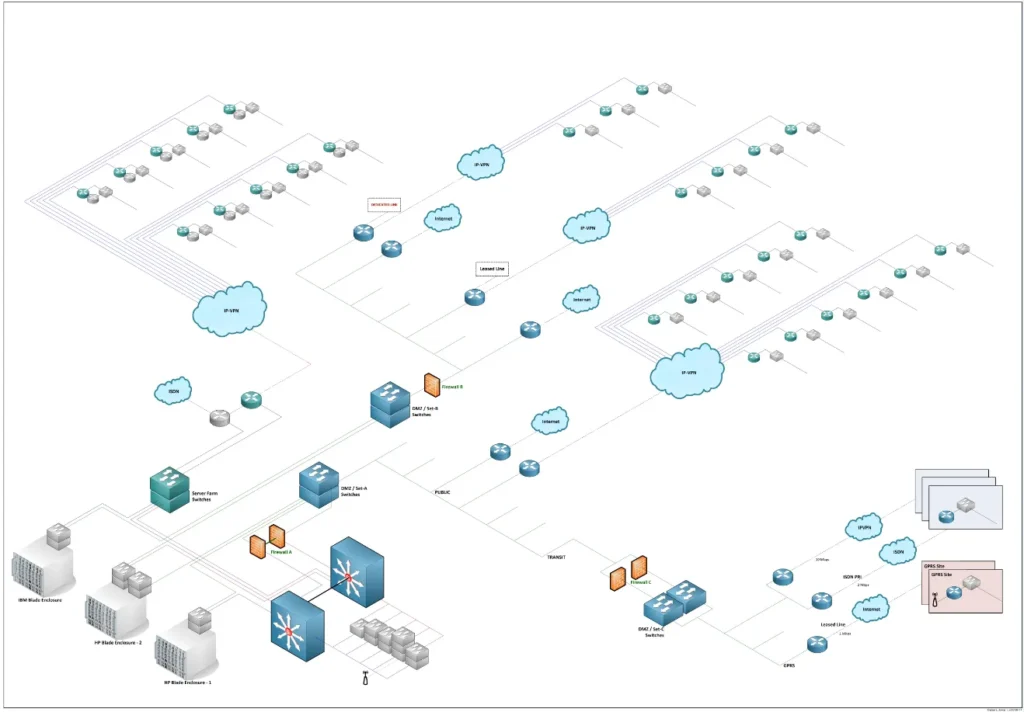
Next, we develop accurate and clear network diagrams, asset inventories, and configuration records, documenting hardware specifications, IP addressing schemes, firewall rules, VPN configurations, system interdependencies, and data classifications. All documentation is organised into a secure, accessible, and version-controlled repository.
Where required, we map your documentation to relevant compliance frameworks, ensuring it meets audit requirements for standards like ISO 27001 and NESA. We also provide tailored policy and procedure documents covering system hardening, incident response, backup strategies, and change management workflows.
Our service includes periodic documentation reviews and updates, so your records remain current as your environment evolves. Whether your infrastructure is entirely on-premise, fully cloud-based, or a hybrid of both, we ensure your documentation reflects reality and supports operational, security, and compliance needs.
By partnering with us, your organisation gains control, clarity, and resilience over its IT operations — reducing risks, improving service continuity, and making audits and troubleshooting far simpler and faster.
🎯 Accurate and accessible IT and security documentation is essential for:
- Operational Consistency: Ensures staff follow defined processes.
- Security Assurance: Demonstrates how systems are secured and risks are managed.
- Regulatory Compliance: Meets mandatory requirements for audits, assessments, and certifications.
- Incident Response: Enables effective, coordinated action during security incidents.
- Knowledge Management: Preserves organisational IT knowledge and operational procedures.
Tasks in this Service
- Review existing IT and security documentation
- Identify missing or outdated documents
- Gather infrastructure and process information from stakeholders
- Develop IT policies aligned to operational and compliance requirements
- Document system and network configurations
- Create an asset inventory register
- Draft procedures for user access management
- Document backup, DR, and recovery processes
- Develop incident response and escalation plans
- Prepare change management and configuration control procedures
- Define security awareness and training materials
- Align documentation formats to compliance frameworks (ISO, NESA, SOC 2, PCI)
- Implement version control and document ownership structure
- Final review and validation with management
- Deliver final signed-off documentation pack
📦 Key Deliverables (depending on the scope)
- IT Policy & Procedure Documents
- Security Policy Set (Access Control, Data Protection, Incident Response, etc.)
- Asset Inventory & Configuration Documentation
- User Access Management Procedures
- Backup & Recovery Process Documentation
- Change Management Procedure
- Incident Response Plan
- Network & Infrastructure Diagrams
- Security Awareness and Training Guidelines
- Final Documentation Pack with Version Control
📌 Compliance Standards That Require Documentation
Several major standards and frameworks require documented policies and procedures:
- ISO 27001: Mandatory documented information for ISMS scope, security controls, and risk treatment.
- NESA (UAE): Requires documentation for cybersecurity governance and operational controls.
- SOC 2: Demands documented policies for security, availability, confidentiality, and privacy.
- PCI DSS: Requires documented processes for cardholder data protection and security controls.
- HIPAA: Mandates security, privacy, and breach notification documentation for healthcare entities.