Infrastructure Assessment
IT infrastructure assessment is required from time to time as an input to decision making – for strategic investments in technologies or for process improvement and optimisation. Organisations engage external parties to do health-checks and assessments for an independent opinion. Typical assessments are generally conducted in the following major phases:
1. Survey and Data Gathering
2. Documentation and Assessment of the Infrastructure
3. Gap Analysis vis-à-vis good practices
4. Recommendations for improvement, configuration changes etc.
5. Presentation of findings, reports; and workshops.
Based on the maturity level, and business requirements (gathered during interviews), we make recommendations or highlight areas which require attention – whether configuration changes, upgrades or a complete overhaul of the systems in question. These recommendations will be guided by good practices, taking into consideration latest technologies and security enhancements, for the overall improvement of IT services.
Recommendations will be made in alignment with enterprise architecture, if a formal definition exists in the organisation; if not, these recommendations will be conducive for such a design in the future. In addition to various documents, we also produce engaging infographics as a part of deliverables.
We help organisations ensure their IT infrastructure is resilient, secure, and aligned with best practices. Our Infrastructure Assessment Service reviews your entire technology environment — from network devices and servers to cloud systems — identifying vulnerabilities, performance gaps, and areas of non-compliance. We deliver actionable recommendations to strengthen infrastructure security, availability, and operational efficiency.
Whether you’re preparing for a compliance audit, migrating to the cloud, or reviewing existing systems, this assessment provides a clear roadmap for infrastructure improvement.
Benefits of Infrastructure Assessment:
- Identify infrastructure vulnerabilities before attackers do
- Ensure alignment with industry compliance standards
- Improve network resilience and system availability
- Reduce risk of downtime, data breaches, and operational loss
- Gain a clear, actionable roadmap for infrastructure improvement
- Support business continuity and disaster recovery planning
- Strengthen cloud and hybrid environment security
- Help prepare for external audits and certifications
- Enhance operational efficiency and scalability
- Build stakeholder and regulator confidence
Deliverables
- Executive Summary Report
- Detailed Infrastructure Assessment Report
- Infrastructure Architecture Review
- Vulnerability and Risk Findings (Optional)
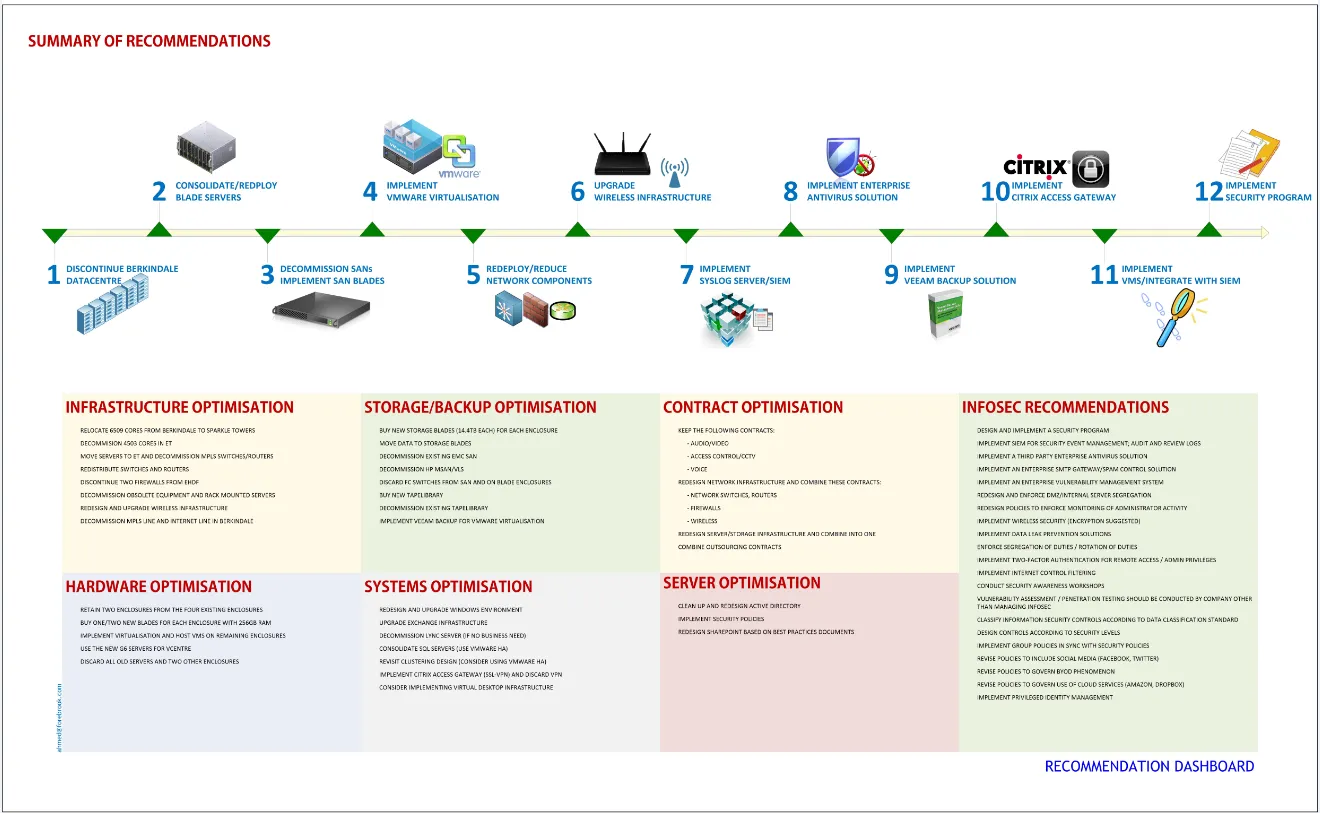
- Recommendations and Roadmap Document
- Final Debrief Presentation
Key Features of Our Assessments
Survey and Data Gathering
Consultants will examine all the components in the IT infrastructure and acquire data by:
– Physical survey of data centres, computer rooms
– Interviews with IT staff
– Inspection of systems, configurations, documentation
Documentation
Work products in this phase include:
– Documentation of servers, networks, applications, services, etc.
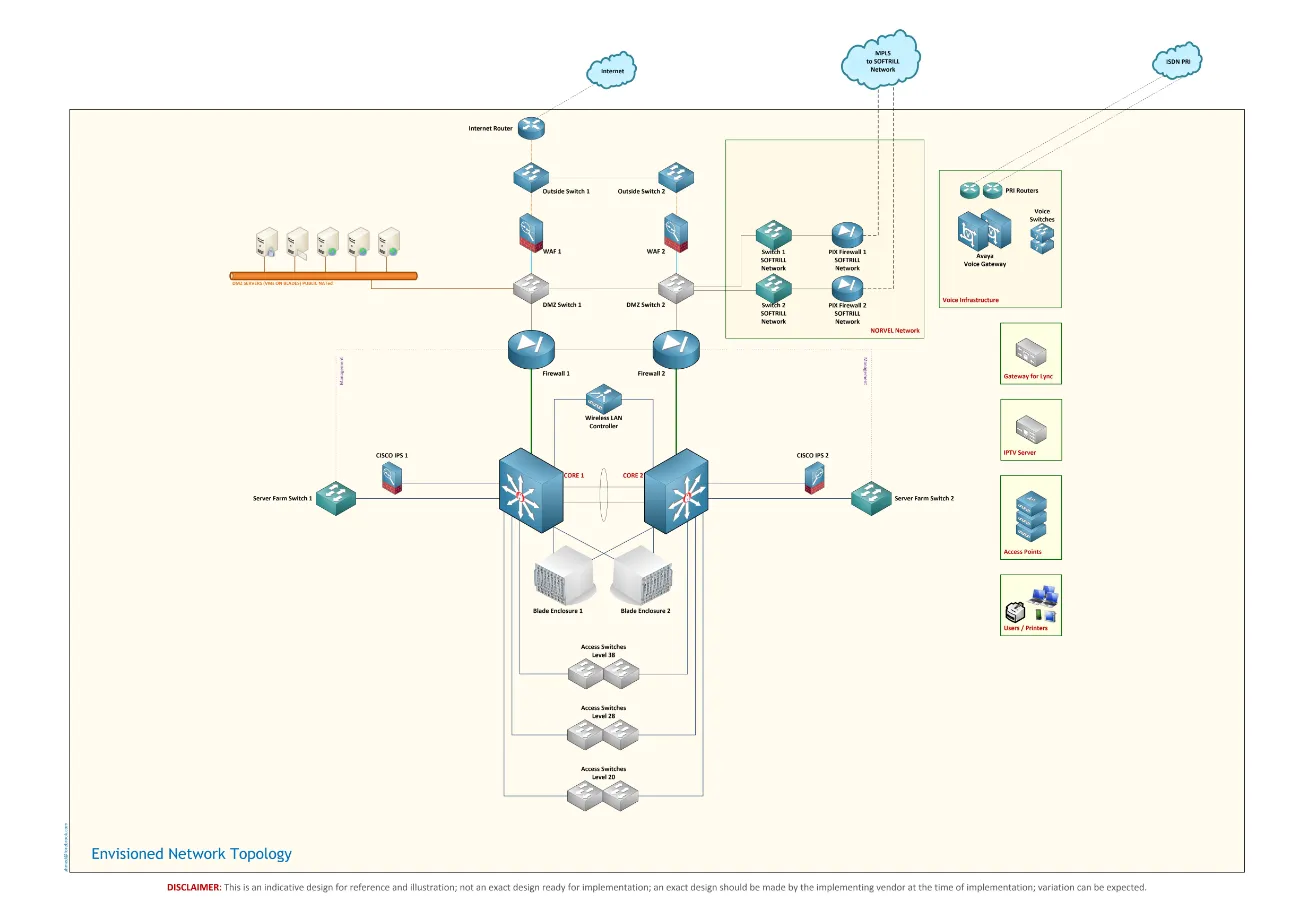
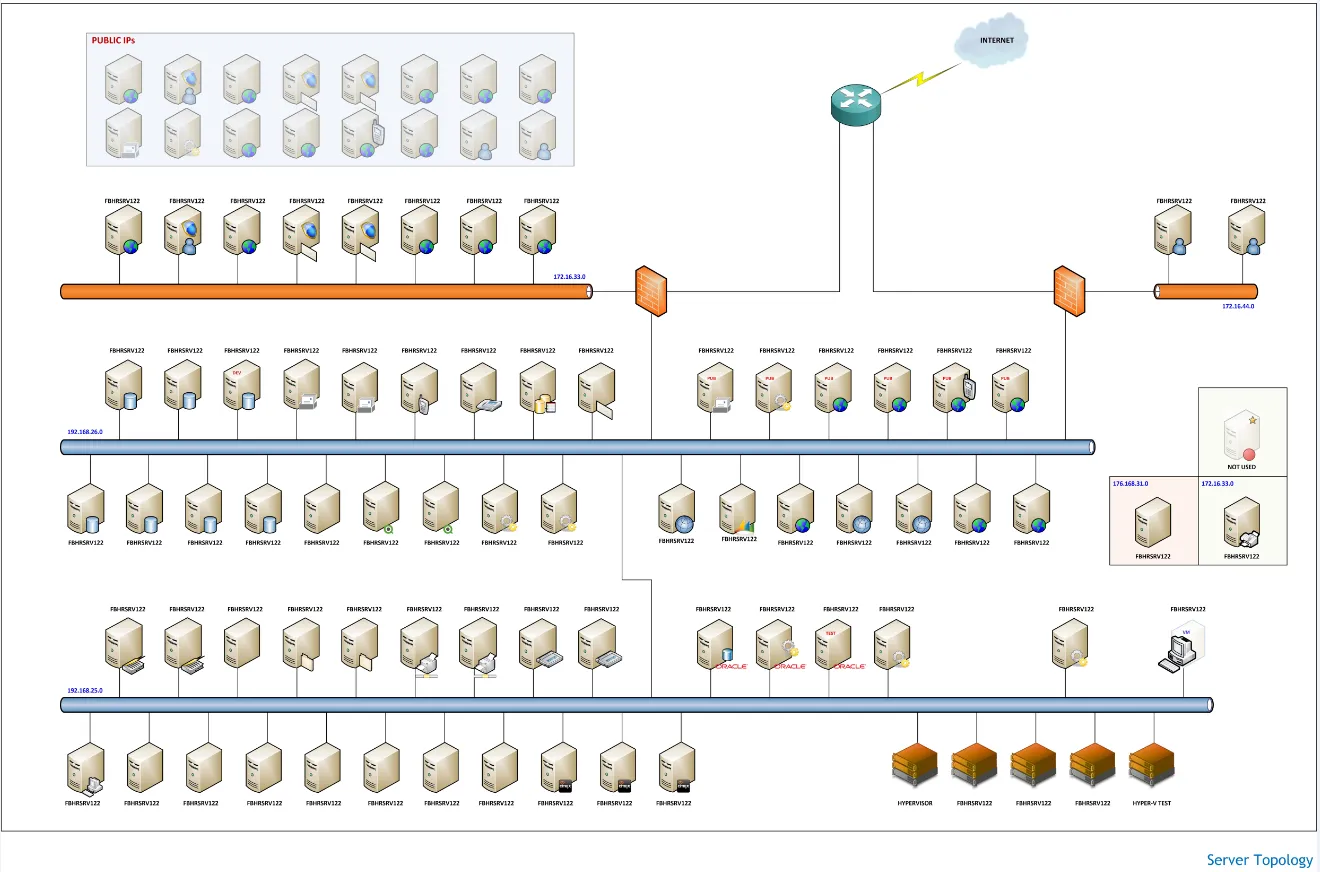
– Topology and connectivity diagrams
– Server and equipment lists
Assessment & Analysis
Adequacy of controls will be tested against
– Controls based on standards/frameworks:
– ISO27001/PCI-DSS/NIST etc
– Test controls in all security domains
– Technology assessment by VA tools
Quality Reports
Summary reports and detailed reports will be submitted. The granularity of reports and types of reports vary according to the scope and requirements of the client.
Recommendations
Based on the business requirements:
– Highlighting areas requiring immediate action
– Configuration changes or system upgrades
– Implementation of new controls
Presentation & Workshop
– Presentation of findings: Executive Summary
– Discussing recommendations with the team
– Workshop with tech and admin teams